KGB-Controlled Website Involved in Cyberattack on Ukrainian Enterprises
3- 22.06.2017, 11:26
- 22,847

Independent journalists have already sent a request to the Security Service of Ukraine.
The Internet domain gomelbest.info and attached mailbox gomel.best@yandex.ru are involved in cyberattacks on state institutions and infrastructures of Ukraine, Belsat informs.
This March CyS Centrum (Ukrainian cybersecurity team) published "Targeted attack on Ukrainian enterprises using the malicious software Ursnif". The report says that on March 14 there were failures in the work of river and sea transport enterprises.
Attackers used ordinary e-mail. Different mail boxes sent letters allegedly from the State Tax Service of Ukraine. CyS Centrum employees intend that this served as a "bait" and forced people to open the letter with the document. Once a user opened it, the malicious software offered to activate the content (run the macro) and after activation the built-in malicious code was launched by itself.
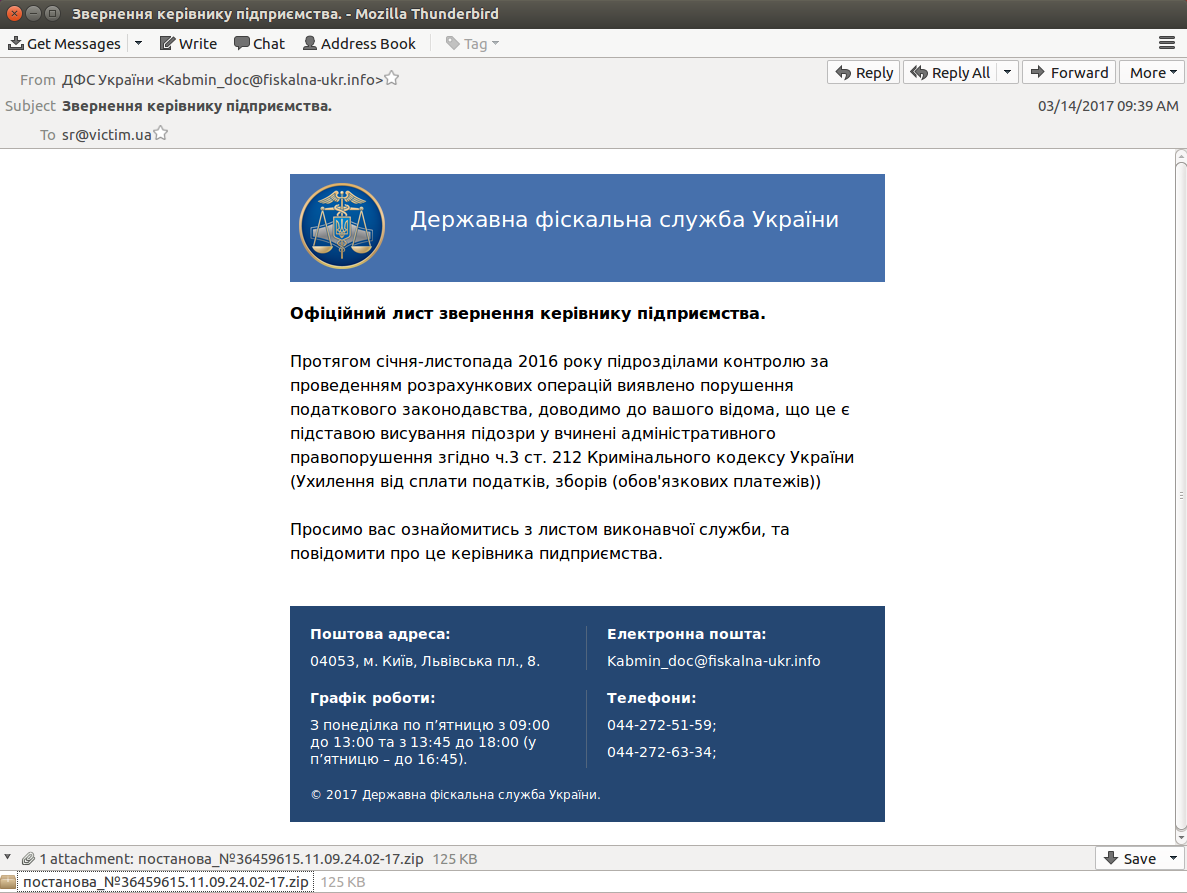
At the next stage Ursnif was downloaded to the computer. Ursnif includes remote execution of various instruction, information and personal data jacking.
At the end of the report experts provide an incomplete list of sites and email addresses one way or another related to cyberattacks. Most of them are registered in Russia. But there is gomelbest.info in the list.
As it became known, gomelbest.info administers directly the KGB admiistration in the Homel region. This was told by the ex-agent of the Belarusian special service Siarhei Vasiliyeu, who used to be administrator of the site for almost 9 years, and now he immigrated to Poland.

"The idea to create the site belonged to the deputy chairman of the regional KGB Aliaksandr Tsitou, he was responsible for the content, and I - for technical support," Vasiliyeu told reporters.
According to Vasiliyeu, after leaving for Poland he turned off the site, but the KGB made a mirror copy and the resource continues work.
We wondered if the site and mailbox under the control of the KGB could be hacked first, and only then attacks started.
"The British company VPS.NET we purchased the server from undertakes to track all hack attempts. If such an attempt is fixed, it is immediately blocked. All similar European and American companies operate like that. We were never hacked during my work there. The site has always been highly protected. I do not even know why the KGB might need all this," he said.
Belsat asked a representative of CyS Centrum for a comment. He talked to a journalist on condition of anonymity.
"We did not set the task to relate the attack to those who did it. Public accusations are not our style. Our specialists concentrate on raising the awareness of citizens and organizations about cyberthreats and developing countermeasures. But we know our cyberenemies and treat them adequately. Even if specific malicious emails have been sent from another mailbox, this box is the part of the same infrastructure with the site you are talking about. In simple words, they should have had better secrecy," the expert says.
In May Reuters reported that Russian hackers were suspected of attacking the power grids of the Baltic States and Ukraine. On May 16 cybercriminals from Russia attacked the site of the presidential administration of Poroshenko, deputy chairman of the department Dmitry Shimkiv stated. He stressed that the attack originated from resources Vkontate and Yandex.
Belarus has not been involved in the high-profile cyberattacks before.
Now Belsat has sent an official request to the Security Service of Ukraine and is waiting for a reply regarding the role of gomelbest.info in this attack.








